February 9, 2008
February 7, 2008
links for 2008-02-07
January 29, 2008
links for 2008-01-29
January 27, 2008
links for 2008-01-27
January 25, 2008
links for 2008-01-25
-
Interesting tool that enables companies and other people to publish press releases on the net
-
PRLog do press releases online
-
Warkitting: the Drive-by Subversion of Wireless Home Routers
January 24, 2008
links for 2008-01-24
January 22, 2008
links for 2008-01-22
-
Excellent article from Wired about AI, the pressures of academia and suicide ...
January 20, 2008
links for 2008-01-20
January 19, 2008
links for 2008-01-19
January 18, 2008
links for 2008-01-18
-
eBook collection for people interested in India, Hinduism, and History
January 17, 2008
links for 2008-01-17
January 8, 2008
links for 2008-01-08
January 7, 2008
links for 2008-01-07
January 4, 2008
links for 2008-01-04
January 3, 2008
links for 2008-01-03
-
... has just given away e-rights to his ebook ... the "digg effect" will help of course ...
-
Possibly the best Nusrat Fateh Ali Khan site on the web ...
January 2, 2008
links for 2008-01-02
December 23, 2007
Hacker's Handbook V3.0
I have had a lot of people ask about whether there would be a "Hacker's Handbook v3.0" as there have been many many changes across the years since I wrote v1.0.
I am pleased to announce that I have just been informed by my editor (god bless him!) that Carlton have given the green light to the 3rd Edition of "Hacker's Handbook" - but in their infinite wisdom are rebranding it as "Cyberthreat Handbook" (bless their little cotton socks!).
Anyhow - I have no idea when they plan to publish it (probably in the Spring) - and now I have to sit down and re-write, edit and generally get off my lazy fat behind and do some real work ...
Anyhow here is the info-sheet used by Carlton along with a mock up of the cover and the back cover blurb.

Since the first edition of Complete Hackers Handbook nearly everything has changed – sometimes for the better and mostly for the worse.The word “Hacker” has been reclaimed by real hackers who like to play with things and make something new of them. The explosion of technology called “Web 2.0” is the result.
Meanwhile the “Black Hat Hackers” have moved on. Hacking is no longer a game for “script kiddies” or computer enthusiasts – but a serious and organised criminal enterprise.
Cyberspace has become occupied by transnational criminal gangs who mount “Phishing” attacks to steal personal information and who use “BotNets” to run “Distributed Denial of Services” (DDOS) attacks on likely targets for “CyberExtortion”.
“CyberActivists” of all creeds and religions battle it out on the Internet using “0 day exploits” and “drive by Trojans” to infect servers and personal computers alike.
During open warfare and times of tension between factions in the real world there is likely to be a corresponding increase in cyber-attacks and web-defacements that affects every Web user by increasing the chances of their computer being attacked.
Finally - “The Balkanisation of the Internet” caused by “Cyber Censorship” - is a problem that affects the Internet at a hidden level, whether it is enforced by “Blacklist” style “CensorWare” programs at a local level or by “Cyber Curtains” that restrict free speech in certain countries (e.g. “The Great Firewall of China”).
Examining the new dangers the Internet faces underscores the point that the Internet is still a vulnerable and fragile technology. These new threats undermine the very nature of the Internet - and may ultimately destroy it as the utility of tools such as email and web browsing decreases to zero - leading to the “Death of the Internet”
The CyberThreat Handbook is the ultimate guide to this intriguing electronic art.
Since Hackers Handbook 1.0 was published the Internet has got more dangerous – with the numbers of attacks accelerating on a daily basis.Cyberspace has been invaded by transnational criminal gangs who mount “Phishing” attacks to steal personal information for Identity Theft and use “BotNets” to run “Distributed Denial of Services” (DDOS) attacks on likely targets for “CyberExtortion”.
These criminal hackers attack computers as a means to an end – so they target people who use the Internet on a daily basis to mount their criminal attacks – placing ordinary users at risk..
The growth of Information Warfare means that CyberJihadis, CyberActivists and Black Hat Hackers funded by secretive intelligence agencies, battle it out on the Internet by infecting servers and personal computers alike.
During open warfare and times of tension between factions in the real world there is likely to be an increase in cyber-attacks and web-defacements that affects every Web user – wherever they are.
These new threats undermine the very nature of the Internet - and may ultimately destroy it as the utility of tools such as email, online commerce and web browsing decreases to zero.
The CyberThreat Handbook is not just Hacker’s Handbook 3.0 – instead it offers the ultimate guide to an art that is no longer just intriguing – but also highly dangerous.Revised and Updated: Phishing, BotNets, CyberExtortion, CyberJihad, Information Warfare, DarkNets, and the links between Hackers and Transnational Crime.
ABOUT THE AUTHOR
Described by the BBC as an “author and chronicler of the hacking scene”, Dr.K is a veteran IT specialist and “old school” hacker who has worked with computers for over 24 years.
Trained in Cognitive Psychology, Psycholinguistics and Artificial Intelligence, Dr.K soon spotted the potential of the Internet and began learning TCP/IP in the days before the “World Wide Web” had even been developed.
Dr.K later worked in IT as part of the team that developed the prototype smartcard systems that later became the “Oyster Card” - before moving on to be an IT specialist for what The Times has called “The World’s Most Famous Secret Society”.
A long time attendee of “London 2600” - Dr.K eventually went on to write Complete Hacker’s Handbook (Carlton 2000, 2nd Edition 2002) and Hackers’ Tales (Carlton 2004).
I'll update here as I have more information - but I guess that writing a book about the Internet is a much more public experience since the 1st Edition and a lot of stuff will spill over into this blog.
Tags: cyberthreat handbook, hackers handbook v3.0, hacking, transnational cybercrime, cybertheats, information warfare, cyberjihad, cybertheft, complete hackers handbook, drk
February 20, 2007
Google Artificial Intelligence
I scanned this a while ago but haven't got round to posting it yet - its a very old cartoon which I used to have on my wall when I was working in an AI lab at Exeter - but thought it was appropriate in the light of the recent news that Google were working in Artificial Intelligence
In a speech Friday night to the Annual American Association for the Advancement of Science conference, Google co-founder Larry Page let slip with a truth we all suspected:“We have some people at Google [who] are really trying to build artificial intelligence (AI) and to do it on a large scale…It’s not as far off as people think.”
Hopefully it will turn out like this ...
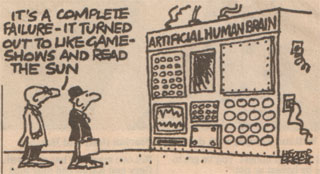
The point being of course, that if you can get a computer to like gameshows and tabloid newspapers - then that really would be a breakthrough in Artificial Intelligence ...
Tags: google, artificial intelligence, gameshows, tabloids
February 17, 2007
This is Not a Pipe ...
I decided to play with Yahoo Pipes to see if it could ease my problems with online news aggravation aggregation.
I've been playing with RSS for the News Machine project for a while now - so I had a few feeds from FeedBurner that i've been using.
To recap for anyone who hasn't read the "News Machine" site - the basic idea is to use Google News to filter the news sources on a set of keywords.
Each set of keywords is thematically related - for example the "Current Obsessions" feed solely filters on the following keywords: cleanfeed, hackers, privacy internet, virus, censorship internet, microsoft security, copyright, drm, riaa, mpaa, piracy internet, piracy sea, malware, blacklists, smartfilter, dmca, spyware, exploit, security internet, and censorware.
Each of these feeds gets a name - e.g. "Current Obsessions" - and for shorthand I've dubbed them "Keyword Cluster Units" (KCU).
News Machine currently uses 10 KCUs and this works very well.
If I drop the feed into e.g. RSS Owl I get a nice listing for each RSS feed - each RSS feed has the "KCU" name as the name of the feed, making it easy to figure out where things have come from - and underneath the "Category" column the keyword shows up as a category.
it makes "the discovery of the new" very easy, my only real problem is that Google News requires an account per every 20 keywords and maintenance is hell if I want to add, delete or (*shudder*) re-cluster any of the keywords.
I've also had problems with online aggravators aggregators, such as Rojo which have a tendency to strip out all the nice keyword information which appears as a "category" ...
The basic RSS dished up from FeedBurner has the following structure for an <item> goes like this:
<item>
<title>
<link>
<guid isPermaLink="false">
<category>
<pubDate>
<description>
.. and of course the text within the <category> tag <\category> is the keyword being searched for in the Google News feed ...
With this in mind I started off making what could possibly be the simplest of Yahoo Pipes feeds - connecting the
the feed for Current Obsessions Keyword Cluster Unit directly into the "pipe output" - like this:
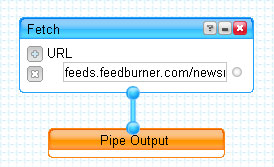
It is probably the simplest pipe there is going - but it is not a pipe at all - once again the all important <category> information field is stripped out - so when I feed the RSS into RSS Owl - I can no longer tell which keyword triggered which story.
The RSS given out by Yahoo pipes filter for an <item> looks like this:
<item>
<title>
<link>
<description>
<pubDate>
Now I might be just being a little picky here - but from my UNIX programming days I remember a "pipe" was just that - it passed everything through the pipe from input to output without changing anything.
What we have here is a "filter" - a pipe that passes some things through unchanged but changes and/or removes others - such as the <category> information ...
I might have missed something - I wondered if the "pipe output" module could be changed to allow stuff through - but it appears that this module is not configurable.
Anyway my conclusion from all this was that "Yahoo Pipes" should be renamed "Yahoo RSS Filters" - if anyone out there has an idea how to get round this limitation - I'd love to here from them.
On the upside, Yahoo Pipes is a nifty network toy for playing around with RSS feeds and aggregating them - even if it doesn't do what I want at the moment - and sometime real soon now I'll be coming back to this topic as I construct a whole KCU inside Yahoo Pipes.
Tags: rss, yahoo pipes, feedburner, rss owl, rojo, news machine, google news
November 8, 2006
All of Your Orifice Belong to Us
After reading the Wired Article that deconstructs the new Microsoft Vista EULA - and in light of the general controversy over the Vista EULA - I came up with a new version ...
All of your orifice belong to usPlease click "YES" to agree or please click "NO" to agree ....
Microsoft - promoting LINUX like there is no tomorrow ...
or maybe ...
Microsoft - a company with a great future behind it ...
Tags: microsoft, linux, vista, eula, wired
October 15, 2006
Performancing & Movable Type
This is the second time in the last day that I've written about Performancing for Firefox.
It's all to do with the blog move which you can read more about here.
Anyway I came to setup Performancing and could not remember where the API key for the XMLRPC interface was stored in Moveable Type
Luckily for me I had made an entry in my internal weblog for future reference when I first setup Performancing earlier this year.
The commonest Movable Type & Perfomancing problem is fixed by this.
I suspect that most MT users don't have an API password set at all for their user.
To set your API password, you'll need to log in to MT, and go to the Main Menu | System Overview | Authors and edit your author profile. The API password is the last field in the profile.
Once you've done that, you can then launch the Account Wizard in PFF and do the following:
For the Server API URL, enter
http://your.domain.com/path/to/mt/mt-xmlrpc.cgi
Enter nothing for the AppKey.
Enter your author username, and the API password that you just set. PFF will now add your blog with no problems.
It works like a charm too ....
Tags: performancing, firefox, moveable type, api, xmlrpc